When I was integrating the Job Scheduler service into my Multitenant Application, I ran into the following JWT Token issue, when the Job Scheduler was calling my CAP action. Means the job creation was already working fine and was also displaying the right tenant for my job, but the Job Scheduler was not able to successfully call the given endpoint. This is the error I got in the logs:
Error: Jwt token with audience: [
'sb-a1e9d3b8-2bee-47db-xxxx-07e5a54aec1e!b180208|sap-jobscheduler!b3',
'uaa'
] is not issued for these clientIds: [
'sb-MyApp-mtdev-App!t180208',
'MyAp-mtdev-App!t180208'
].
After reading some of the great blogs from Carlos Roggan, I noticed that I forgot to grant the Job Scheduler the necessary authority to actual call my CAP action. So I added the following lines to the xs-security.json file
{
"name": "$XSAPPNAME.jobscheduler",
"description": "Scope for Job Scheduler",
"grant-as-authority-to-apps": [
"$XSSERVICENAME(job-scheduler)"
]
}
and also annotated my CAP action using the new scope @(requires: ['jobscheduler']).
I redeployed everything, but the issue still persists. 🙁
Turned out, for the standard plan, tokens are cached in Job Scheduler up to 12 hours.
https://help.sap.com/docs/job-scheduling/sap-job-scheduling-service/secure-access?locale=en-US
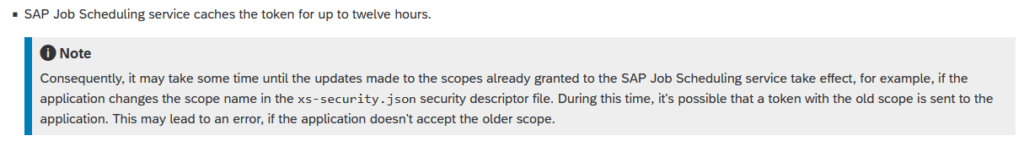
After waiting 12 hours, the endpoint was successfully called by the Job Scheduler. 🙂
