TRY.
DATA(messsage_handler) = NEW cl_hrpa_message_list( ).
cl_hrpa_masterdata_enq_deq=>enqueue_by_pernr( tclas = cl_hrpa_tclas=>tclas_employee
pernr = 1
message_handler = messsage_handler ).
cl_hrpa_masterdata_enq_deq=>dequeue_by_pernr( tclas = cl_hrpa_tclas=>tclas_employee
pernr = 1 ).
CATCH cx_hrpa_violated_assertion.
ENDTRY.
Category: SAP
SAP
[HR] Buchungsbelege anzeigen/analysieren
Hilfreiche Reports:
- SAPMPCP0 – Buchungsläufe bearbeiten (TCode PCP0)
- H99CWTR0 – Lohnarten Reporter
- RPCIP_DOCUMENT_ANALYSE – Buchungsbelege analysieren
- RPCIPD00_FRAME – Details zu Belegzeilen anzeigen
Einige relevante Tabellen:
- PPDHD – Überleitung FI/CO: Kopf des Belegs
- PPDIT – Überleitung FI/CO: Zeilen des HR-Zwischenbelegs
- PPDIX – Überleitung FI/CO: Indextabelle der HR-Zwischenbelege (Verknüpfung zwischen PPDIT und PPOIX)
- PPDST – Überleitung FI/CO: Substituierte Kontierungsobjekte
- PPOIX – Index Abrechnungsergebniszeile -> Buchungszeile
- PPOPX – Index alte <-> neue Belegzeile für ‘P’-Ergebnisse
- PEVST – Abrechnungsauswertungsläufe
- PEVAT – Attribute von Auswertungsläufen
- PEVSH – Historie von Abrechnungsauswertungsläufen (STATUS = 40 Überleitung an FI)
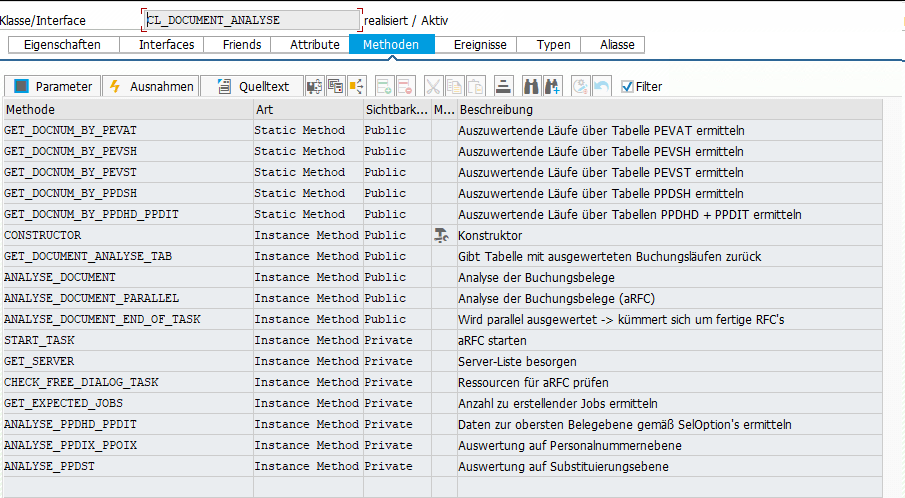
Die Klasse CL_DOCUMENT_ANALYSE hilft die Verknüpfung der Tabellen zu verstehen
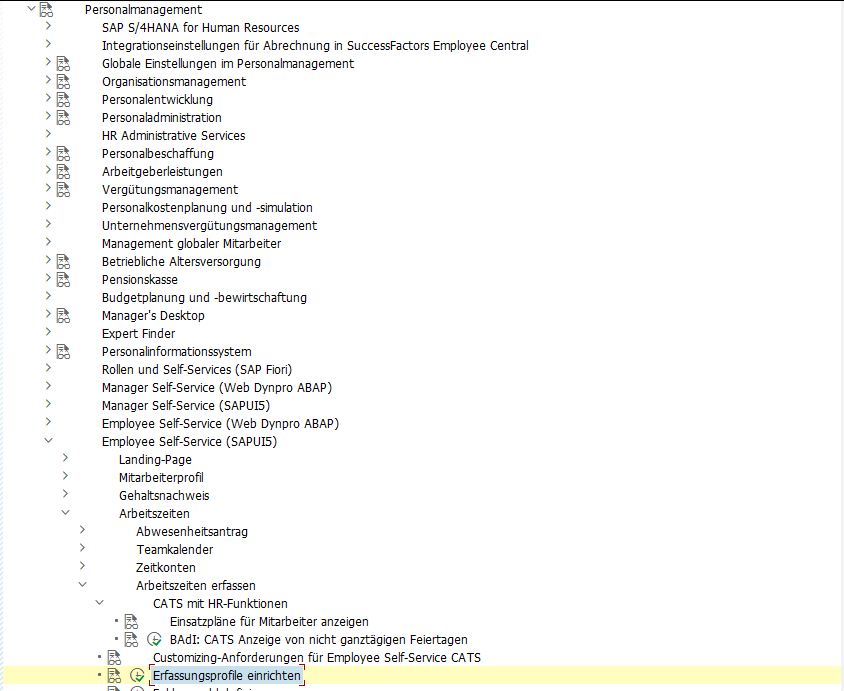
[HR] Zeiterfassung: Kollisionsprüfung aktivieren
SPRO → Personalmanagement → Employee-Self-Service (SAPUI5) → Arbeitszeiten → Arbeitszeiten erfassen → Erfassungsprofile einrichten
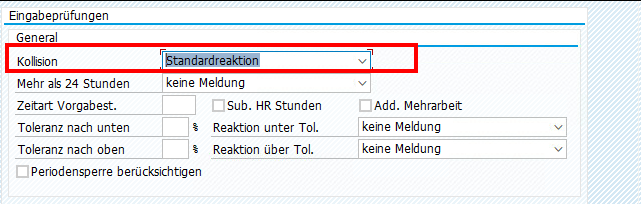
[Fiori] FPS – Feature Pack Stack
In the SAP Fiori Apps Reference Library, you have to select the target system on which the app is to be installed. You can choose between different major releases and also between different FPS’s.
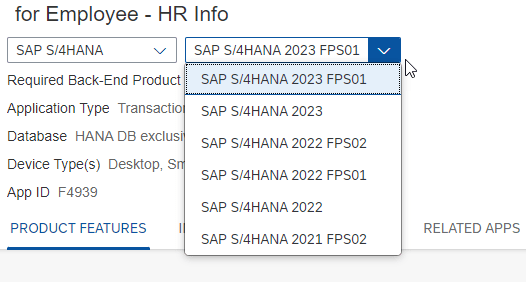
These feature packs are smaller, targeted updates delivered between major releases of S/4HANA. To check if a Feature Pack is installed on your system, go to
System → Status → Button Product version → Tab Installed Product versions → Column SP / FTP Stack
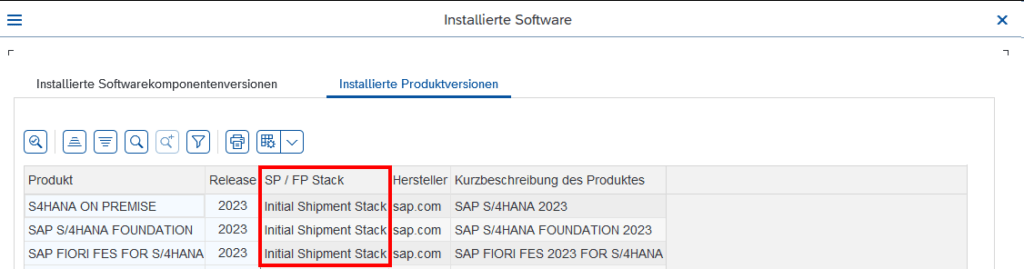
In this case, no additional FPS is installed.
[BTP] Change S-User Password
When testing API Endpoints of applications running on BTP, it can be necessary to authenticate using the right S-User credentials. In such a scenario, the Universal ID password will not help.
Universal ID password can be changed via https://accounts.sap.com (will forward to the Standard SAP ID Service)
A specific S-User password can be changed via https://account.sap.com (will forward to Manage my Account, where you see the different S-User and P-User, linked to your Universal ID)
[Workflow] AC Rule
Recently, I had the task of assigning a workflow decision step to some users that were customized in a Z-Table. Normally I would have done this, by creating a container element “Actors”, a task that calls a method to return these Actors and use these Actors in the decision step. But this time I tried a custom AC Rule for the first time and I must say it was much easier than expected.
To begin, simply create a function module. The function module only needs two table parameters, AC_CONTAINER and ACTOR_TAB. They can be copied from RH_GET_ACTORS or GM_GET_RESP_FROM_INTERNAL. There you can also check, how to access the AC_CONTAINER table, if you need any input values from the WF. In my case, I just had to read the Z-Table and return the result via ACTOR_TAB.
SELECT * FROM ztable INTO TABLE @DATA(lt_table).
LOOP at lt_table INTO DATA(ls_table).
"you can also check if the provided user exists by using function module 'SUSR_USER_CHECK_EXISTENCE'
APPEND VALUE #( otype = 'US' objid = ls_table-userid ) TO actor_tab.
ENDLOOP.
IF lines( actor_tab) = 0.
RAISE nobody_found.
ENDIF.
Then simply go to tcode PFAC, create a rule, provide the function module and check the flag box at the end.
In the PFAC transaction, you can also simulate the rule resolution.
If everything works fine, add the new created rule to the decision step.
And done. Really straight forward.
[ABAP] Escape URL
DATA(path) = escape( val = 'https://url.com/path/with/a space/in/it'
format = cl_abap_format=>e_url ).